IT service management (ITSM)
What is IT service management (ITSM)?
IT service management (ITSM) is a general term that describes a strategic approach to design, deliver, manage and improve the way businesses use IT. ITSM includes all the discrete activities and processes that support a service throughout its lifecycle, from service and change management, to problem, incident, asset and knowledge management.
An IT service enables access to information and processes to accomplish important business goals or otherwise provide value. IT services include the deployment and support of enterprise applications, such as Exchange Server; architecting and optimizing IT infrastructure such as storage, networking and cloud resources; and the creation and management of processes such as help desk support and troubleshooting procedures.
IT teams must create, deploy, manage, optimize and potentially retire each service, with input from the business. Each service can have an associated service-level agreement, which codifies performance and availability expectations and the ramifications if the service falls below these expectations.
ITSM benefits include business-IT alignment, predictable IT performance and costs, and continual improvement of IT effectiveness and capabilities. When IT processes are orderly and well-managed, organizations can spend less time on proverbial firefighting and devote it to strategic initiatives.
ITSM and IT service delivery
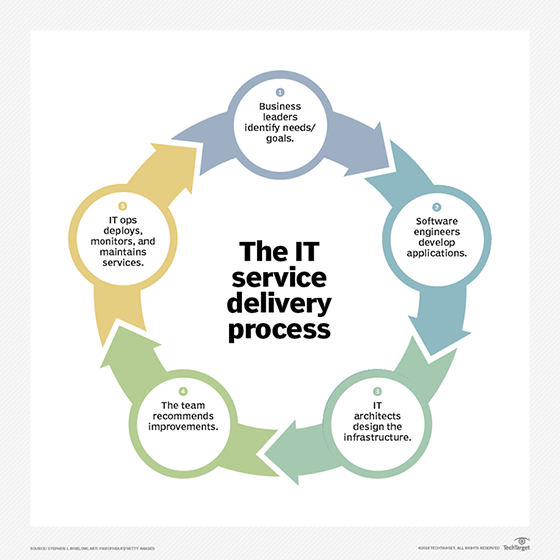
IT service delivery is generally discussed in terms of providers and customers, who interact via the IT service desk. An IT service provider selects, designs, deploys and operates the service. The provider can be an internal IT department or a third-party specialist. An IT service customer is any consumer of those services, such as the employee who accesses email through the organization's Exchange Outlook interface. IT organizations generally offer customers an IT service catalog, a list or menu of available services.
There are many roles within the IT service desk. IT services typically start with a need and strategy, which demands clear guidance from business and IT leaders. Services must then be architected and deployed, requiring the expertise of IT hardware and software application engineers. Services must be monitored and tracked, and problems remediated by IT administrators and helpdesk staff. KPIs for the service must be communicated, with recommendations for service changes and improvements, to the business that uses them.
ITSM and IT service delivery sometimes are used interchangeably. However, ITSM emphasizes IT service operation and improvement, while IT service delivery focuses on the quality of the work and meeting customer expectations. Additionally, the terms ITIL and ITSM typically are conflated. ITIL is a well-known and popularized ITSM framework.
ITSM processes
To manage IT services, organizations must control the service's capabilities, how it performs, changes to it and what happens when it experiences problems. These processes fall under several main categories, primarily defined by ITIL, but appearing in various forms in other ITSM frameworks.
- Change management. When a service is out of step with business expectations, it must be modified, expanded or otherwise altered. IT must determine how these changes will affect the service deployment, implement them appropriately, then monitor if the changes have the intended effect. Release management can be grouped with change management or treated as a separate process.
- Asset management. Services require software and hardware assets to function. These assets should be tracked, updated appropriately and mapped to show how they interact. Configuration management, capacity management and asset management deal with these concerns and can be blended or separate processes.
- Project management. IT services transition between various stages of the lifecycle at different times and different speeds. Project management skills enable IT organizations to maintain orderly services and avoid problems, such as outdated systems or shadow IT.
- Knowledge management. Knowledge management crosses into the other ITSM processes and helps avoid duplicated work and discovery by organizing and making available information about IT services.
- Incident management. When an IT service is disrupted by performance issues or an outage, the IT service desk must address the issue, restore service availability, make improvements and codify procedures to prevent reoccurrence. Incident management helps solve these problems.
- Problem management. A problem is the root cause of an incident. An IT organization might remediate an incident but not fix the problem, leading to future incidents. Problem management is a way to permanently fix issues to improve service delivery and performance.
ITSM software and tools
ITSM's various processes and functions demand the use of a range of tools. ITSM software manages the workflow of service delivery, and can enable communication between customers and providers. This category includes process orchestration, help desk and service desk tools. Examples of ITSM tools include Axios Systems' Assyst, ServiceNow and BMC Remedy.
Other systems management tools aid ITSM processes. These tool categories include CMDB, asset management, license management, application performance monitoring and log analytics software.
Popular ITSM frameworks
ITSM typically is associated with the service lifecycle outlined in ITIL v3. ITIL processes cover how to set a strategy, create a design, manage change, handle service operation and management, and make continual improvements to the service. However, there are numerous other frameworks and standards used for ITSM and IT service delivery. The goal of every IT service management framework is to ensure that the right ITSM processes, people and technology are in place so the organization can meet its business goals.
ITIL. The ITIL framework provides best practices for aligning IT with business needs. ITIL is the most widely used framework for IT process management and has five parts: Strategy, Design, Transition, Operations and Continual Service Improvement. Ongoing development for ITIL is vested in Axelos, a joint-venture company created by the U.K. Cabinet Office and Capita PLC. ITIL was created because there was a need for ITSM best practices in the late 1980s, and it has since become the de facto framework used by many organizations across the world. As of publication, the latest version of the framework is ITIL v4.
COBIT. COBIT, which originally stood for Control Objectives for Information and Related Technologies, is a framework to develop, implement, monitor and improve IT governance and management practices. The IT Governance Institute and the Information Systems Audit and Control Association (ISACA) publishes the COBIT framework.
Microsoft Operations Framework (MOF). This series of documents guides IT professionals through the processes to create, implement and manage efficient and cost-effective services. Like ITIL, MOF includes guidelines for the entire lifecycle of an IT service, from concept to retirement or replacement.
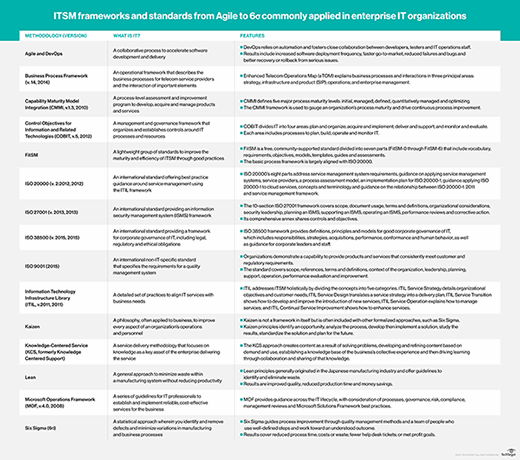
Six Sigma. Motorola introduced the Six Sigma management framework, and it is applied to various disciplines. The framework emphasizes setting extremely high objectives, collecting data and analyzing results to a fine degree as a way to reduce defects in products and services.
ISO 20000. ISO provides global standards, such as ISO 20000, which describe the requirements for an ITSM system. Although the British Standards Institutions developed the standard to mirror best practices described within the ITIL framework, it also supports other frameworks, such as MOF.
The Open Group Architecture Framework (TOGAF). This structured approach to ITSM is for companies seeking to organize and govern their implementation of technology, particularly software technology. The Open Group, an independent industry association, created and maintains TOGAF.







